Benefits
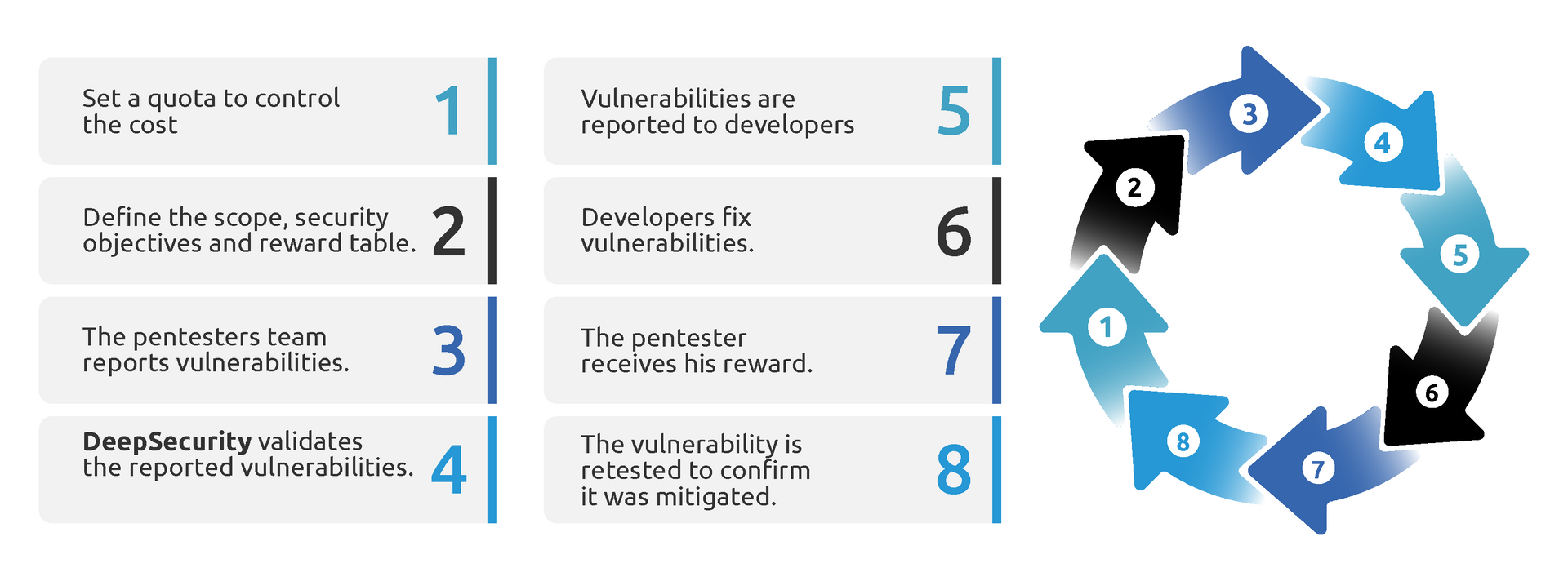
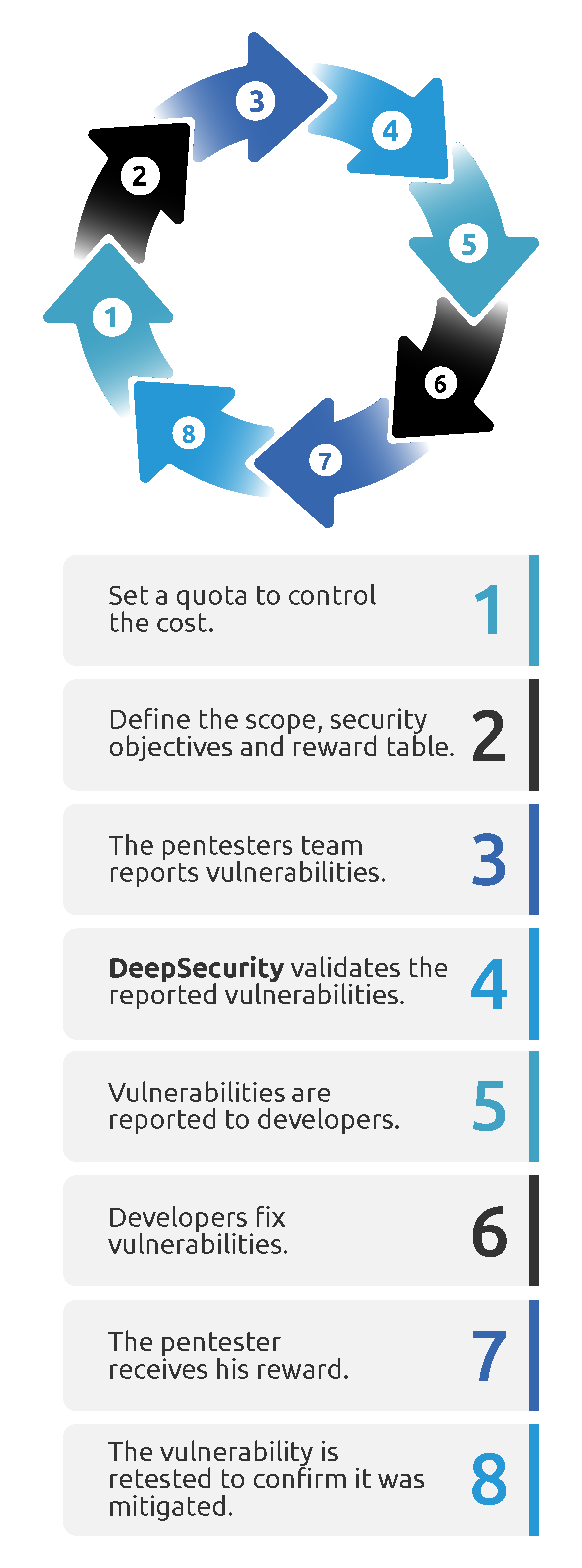
How does it work?
Secure your online services more effectively
It is an effective long-term complement alternative to penetration testing and security audits, and allows even mid-sized businesses that cannot afford expensive testing to test their IT security.
While penetration testing provides the company with an overview of its security as of a given date, the bug bounty program ensures ongoing security assessments by a team of renowned cybersecurity experts.
What types of online services should I try with BUG BOUNTY from DEEPSECURITY?
- Online services that use sensitive user data (for example, personal, payment or accounting data), e-store or its part (new product category, new feature,...)
- CRM Systems
- Online payment gateway
- A new feature of a website
- An online application or service that works over the Internet
- Third party solutions located on your servers
- In general, any new product that appears on the Internet or extracts data from online databases
Improve the security of your online projects!
Do you want to join the DeepSecurity bug bounty program but don't know how to get started?
Go to our Contact section and write to us. If you want to create your first bug bounty program directly in DeepSecurity, we can help you with the templates we have prepared for you together with our security experts.

Pay only per reported vulnerability
The scope of this service includes security bugs for web applications, mobile applications, APIs, and more. Companies such as Google, Facebook, Twitter and PayPal participate in these types of programs. DeepSecurity follows this philosophy and responsible disclosure policy.