Industrial Cybersecurity (OT/ICS)
Strengthening OT security
Our commitment is to detect and neutralize vulnerabilities before they become threats, ensuring critical infrastructures for a safe future.

We understand the importance of protecting every layer of your critical infrastructure. Our specialized operational technology (OT) and cybersecurity services are designed to accompany you throughout the entire cybersecurity lifecycle, ensuring the integrity and protection of your most sensitive systems.
We have created an offer based on the real needs of clients seeking OT cybersecurity consulting services.
Our offer includes:
Benefits
How does DeepSecurity work on OT cybersecurity?
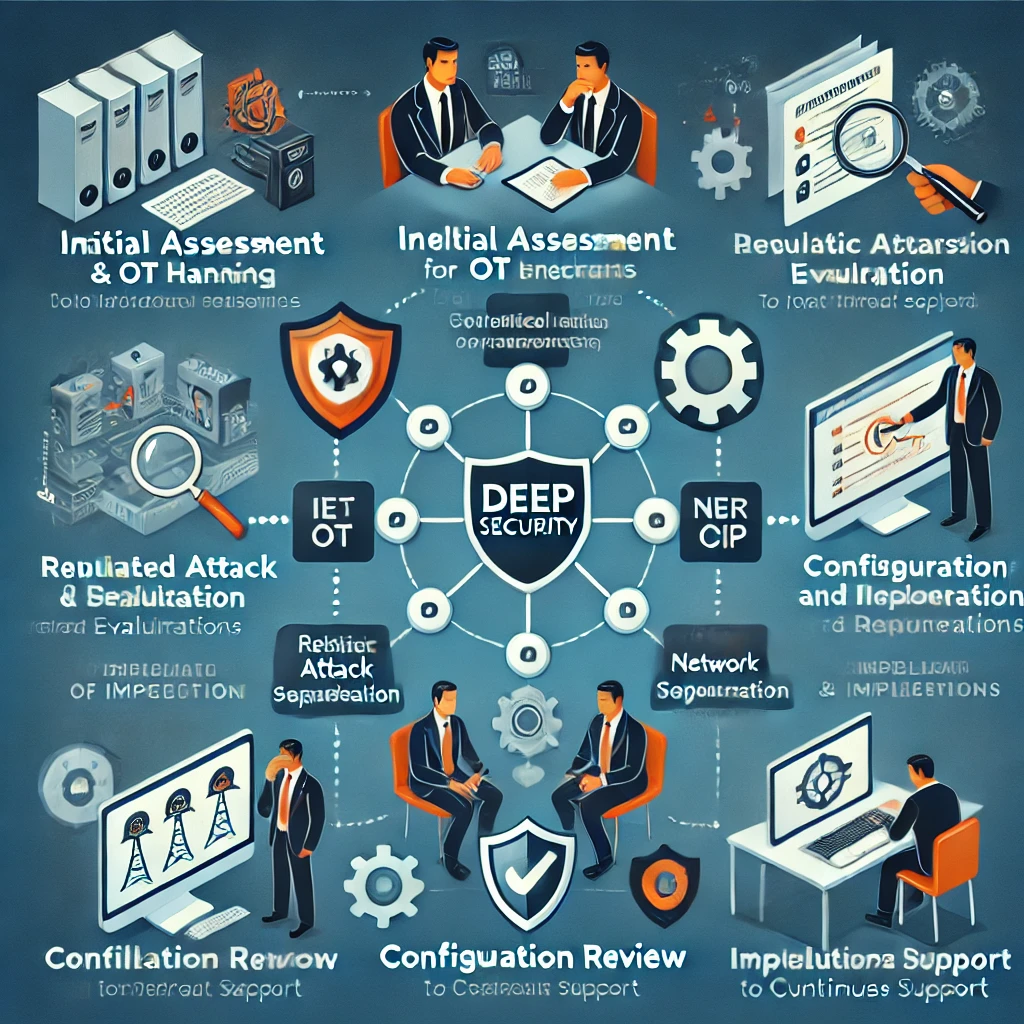
At DeepSecurity we offer a structured approach to protecting our clients’ IT and OT environments. Our process includes:
- Initial Assessment and Planning: We meet with the client to understand their needs and define security objectives.
- Realistic Attack Simulation (Ethical Hacking): We perform controlled intrusion tests on corporate and OT networks to identify critical vulnerabilities.
- IT/OT Network Segmentation Assessment: We analyze the effectiveness of segmentation to prevent the spread of threats and protect critical systems.
- Configuration Review and Regulatory Compliance: We verify configurations and records to comply with standards such as IEC 62443 and NERC-CIP.
- Report Generation and Validation: We create detailed reports of findings and recommendations, reviewed by senior consultants to ensure quality.
- Implementation of Improvements: We assist the client in the application of recommendations and validate the implemented solutions.
- Continuous Monitoring and Support (optional): We offer continuous monitoring services to maintain a secure environment.
This approach allows us to provide comprehensive and customized protection, ensuring security and compliance at every stage of the cybersecurity cycle.
While penetration testing provides a company with an overview of its security at a given date, the bug bounty program ensures ongoing security assessments conducted by a team of recognized cybersecurity experts.

Experts with more than 15 years of experience in Cybersecurity
We are a company specialized in offering cybersecurity solutions and services, with a team made up of renowned experts who guarantee the best option in offensive security and protection for your brand, your data and your collaborators against advanced threats.